A friendly reminder to never trust manufacturers privacy protections.
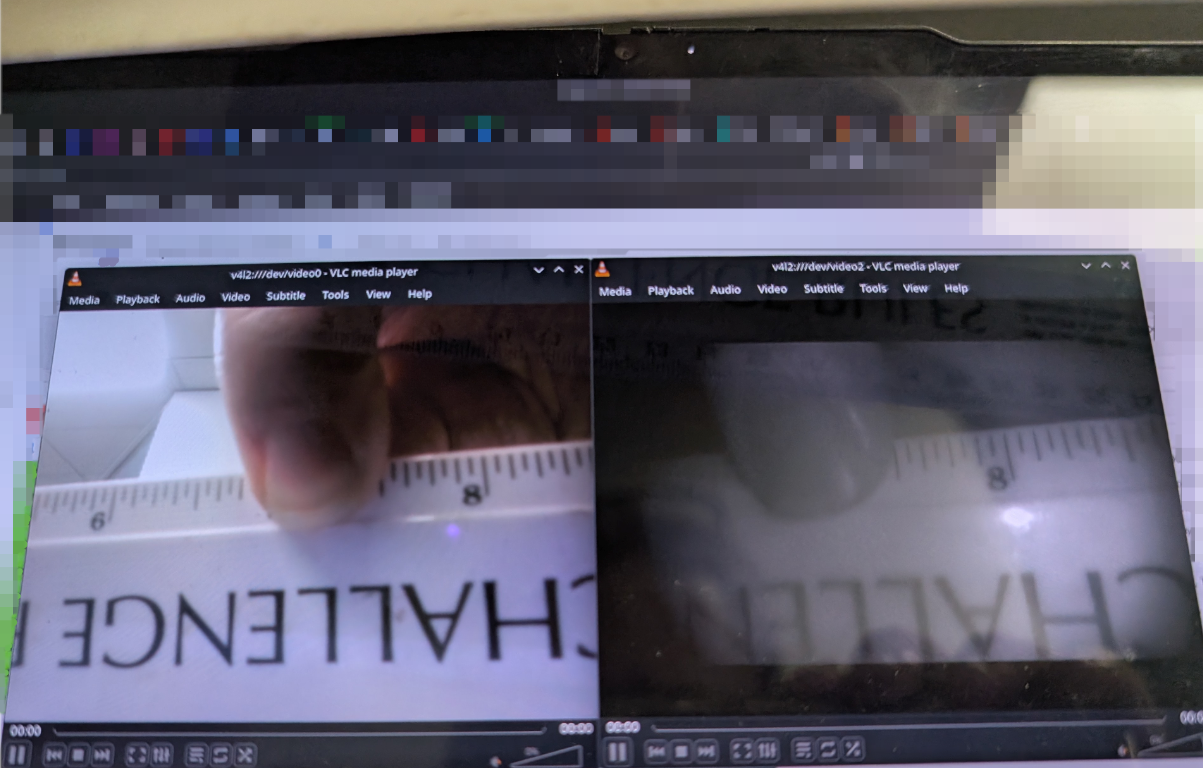
I was recently attempting to get an external camera functioning, so I started polling various video devices sequentially to find out where it appeared and stumbled across a previously unknown (to me at least) camera device, right next to the regular camera that is not affected by the intentional privacy flap or "camera active" LED that comes built in.
I had always assumed this was just a light sensor and didn't think any further about it.
The bandwidth seems to drop dramatically when the other camera is activated by opening the privacy flap, causing more flickering.
This was visible IRL and wasn't just an artifact of recording it on my phone.
I deliberately put my finger over each camera one at a time to confirm the sources being projected.
A friend of mine suggested this may be related to Windows Hello functionality at a guess but still seems weird to not be affected by the privacy flap when its clearly capable of recording video.
dmidecode tells me this is a LENOVO Yoga 9 2-in-1 14ILL10 (P/N:83LC)
Command I used for anyone to replicate the finding. (I was on bog standard Kali, but I'm sure you'll figure out your device names if they change under other distros):
vlc v4l2:///dev/video0 -vv --v4l2-width=320 --v4l2-height=240 & vlc v4l2:///dev/video2 -vv --v4l2-width=320 --v4l2-height=240
#Cyber #Security #Infosec #Lenovo #Privacy #Hacking